Fix: RemoteIOT SSH Key Issues On Raspberry Pi! A Quick Guide
Is your Raspberry Pi feeling more like a brick than a brain these days, thanks to a stubbornly unresponsive SSH connection? It's time to ditch the frustration because the "remoteiot platform ssh key not working" is not an insurmountable problem.
It's a solvable puzzle, a challenge that, when conquered, unlocks a world of possibilities for your IoT projects. The power of remote access, crucial for managing Raspberry Pi devices scattered across homes, offices, or even remote locations, hinges on the reliability of Secure Shell (SSH) keys. And when those keys falter, the entire system grinds to a halt. But fear not! By understanding the essential role of SSH keys, methodically pinpointing common culprits behind connectivity issues, and implementing the appropriate troubleshooting strategies, you can restore secure remote access to your Raspberry Pi and reignite your IoT ambitions. This article acts as your guide, illuminating the path to a secure and manageable IoT infrastructure, leveraging the power of the RemoteIoT platform and the inherent versatility of the Raspberry Pi.
| Category | Information |
|---|---|
| Topic | RemoteIoT Platform SSH Key Management |
| Related Technology | Raspberry Pi, Internet of Things (IoT), Secure Shell (SSH) |
| Key Benefit | Secure remote access and management of Raspberry Pi devices. |
| Problem Addressed | SSH key issues preventing remote access. |
| Solution | Troubleshooting steps and best practices for SSH key management within the RemoteIoT platform. |
| Reference Website | Raspberry Pi Official Website |
The ever-expanding universe of the Internet of Things (IoT) demands airtight security measures. RemoteIoT platform SSH key management has emerged as a vital cornerstone in safeguarding Raspberry Pi devices operating in remote environments. As connectivity weaves deeper into the fabric of our lives, ensuring secure communication and controlled access to these devices becomes paramount. Passwords, once the standard, are increasingly vulnerable to brute-force attacks and phishing schemes. SSH keys offer a far more robust alternative, employing cryptographic algorithms to verify identity and encrypt communication channels. This proactive security stance is not merely a recommendation; it's a necessity for protecting sensitive data and maintaining the integrity of your IoT network.
- Bollywood Filme 2024 Die Komplette Liste Tophits
- Vega 2023 Streamen Besetzung Amp Handlung Jetzt Mehr Erfahren
But what happens when the very keys meant to secure your kingdom suddenly refuse to turn the lock? The "remoteiot platform ssh key not working" scenario can manifest in various ways: connection timeouts, permission denied errors, or even complete inability to establish an SSH session. Diagnosing the root cause requires a systematic approach, eliminating potential issues one by one. Before diving into the technical intricacies, it's crucial to grasp the fundamental principles of SSH key authentication. SSH keys operate on a public-key cryptography system. A key pair is generated, consisting of a public key and a private key. The public key is placed on the server (in this case, the Raspberry Pi running the RemoteIoT platform), while the private key remains securely on the client machine attempting to connect. When a connection is initiated, the server uses the public key to encrypt a challenge, which only the client with the corresponding private key can decrypt. This process eliminates the need for passwords, enhancing security and streamlining the login process.
By default, SSH key management is often fragmented and complex, leading to potential vulnerabilities. Unmanaged SSH keys are prime targets for malicious actors seeking unauthorized access. Imagine a scenario where multiple developers have access to a fleet of Raspberry Pi devices, each using their own set of SSH keys. Tracking, rotating, and revoking these keys becomes a logistical nightmare, increasing the risk of compromised credentials. The RemoteIoT platform addresses this challenge head-on by providing centralized SSH key management capabilities. With RemoteIoT SSH key management, you can centrally manage and discover all authentication keys and SSH login files. This centralized control empowers administrators to maintain a comprehensive overview of SSH key usage, enforce security policies, and respond swiftly to potential threats.
Managing remote devices like Raspberry Pi can be particularly challenging, especially when considering security and accessibility. Picture a network of sensors deployed in a remote agricultural setting, each relying on a Raspberry Pi for data processing and communication. Gaining secure access to these devices for maintenance, updates, or troubleshooting can be a logistical hurdle. The RemoteIoT platform offers a robust solution by enabling SSH key management for Raspberry Pi devices. This ensures secure access and efficient remote management, which is crucial for developers and IT professionals responsible for maintaining these distributed systems. The platform essentially acts as a gatekeeper, controlling who can access which devices and under what conditions.
- Movierulz Kostenlos Filme Streamen Alle Infos Alternativen
- Filmywap Co Kein Ergebnis Tipps Alternativen
So, how exactly does the RemoteIoT platform leverage SSH keys to achieve this secure communication? The platform uses SSH keys to secure communication between IoT devices and the central server. When a new device is added to the platform, it automatically generates an SSH key pair. The public key is then securely uploaded to the server, while the private key is stored with utmost care on the device itself. This initial handshake establishes a trusted connection, allowing for secure data transfer and remote control. The RemoteIoT platform essentially automates the key management process, minimizing the risk of human error and ensuring consistent security across your entire IoT deployment.
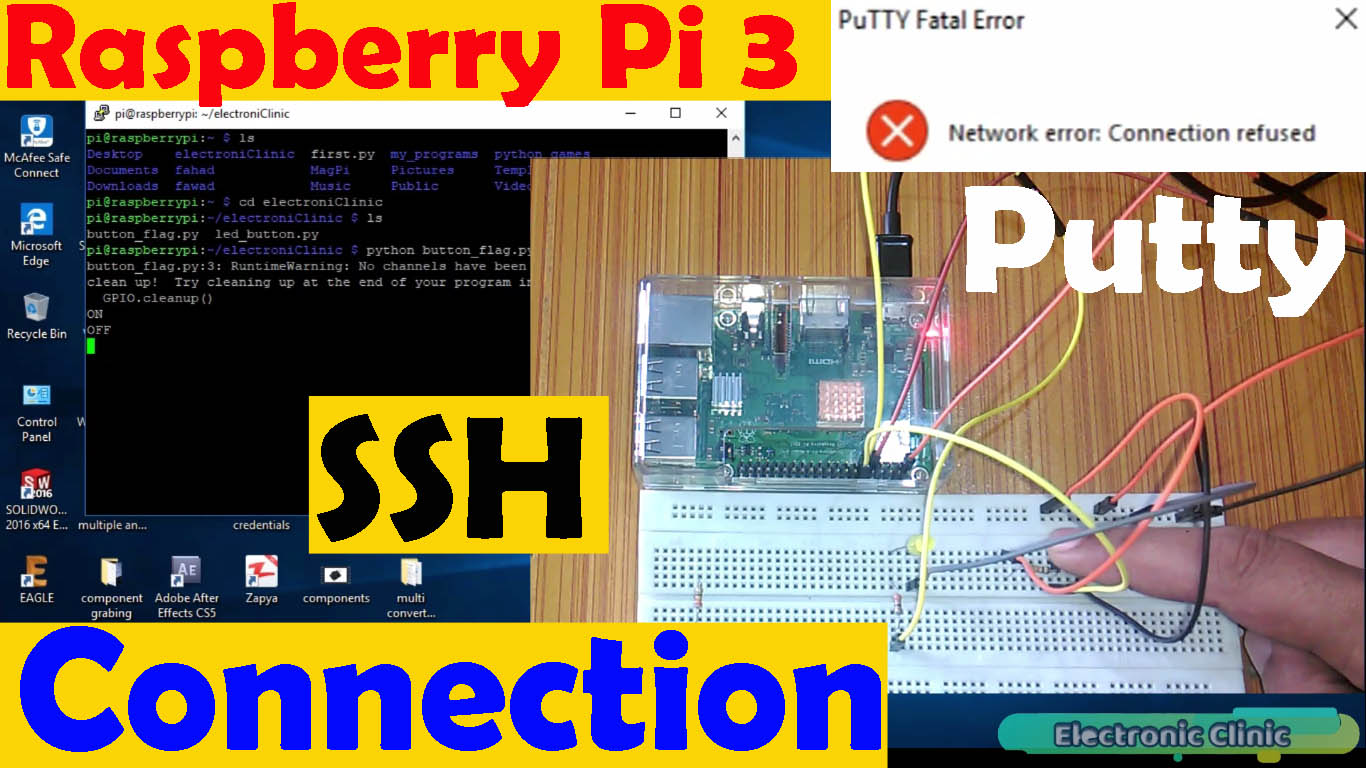
Now, let's address the elephant in the room: the "remoteiot platform ssh key not working" scenario. If you suspect that SSH keys are the root cause of your connectivity woes on your Raspberry Pi, generating new keys is a logical next step. This process is straightforward, but requires meticulous attention to detail to ensure everything is configured correctly. First, ensure that you have the necessary tools installed on your client machine, typically OpenSSH. Then, use the `ssh-keygen` command to generate a new key pair. Choose a strong passphrase to protect your private key. Once the keys are generated, copy the public key to the Raspberry Pi. This can be done using the `ssh-copy-id` command, or manually by appending the contents of the public key file to the `~/.ssh/authorized_keys` file on the Raspberry Pi. Remember to set the correct permissions on the `.ssh` directory and the `authorized_keys` file to prevent unauthorized access. A single incorrect permission can render the entire SSH key authentication process useless.
Beyond generating new keys, several other factors can contribute to SSH key authentication failures. A common culprit is incorrect file permissions. The `.ssh` directory on the Raspberry Pi should have permissions set to `700` (drwx------), while the `authorized_keys` file should have permissions set to `600` (-rw-------). Any deviation from these permissions can prevent SSH from properly authenticating the connection. Another potential issue is incorrect ownership. Ensure that the `.ssh` directory and the `authorized_keys` file are owned by the user account that you are using to connect via SSH. Using the `chown` command to correct ownership issues can often resolve perplexing SSH key problems.
Furthermore, network connectivity issues can masquerade as SSH key problems. Before delving into key-related troubleshooting, verify that you can ping the Raspberry Pi from your client machine. If ping fails, the issue lies within your network configuration, not necessarily with the SSH keys. Check your firewall settings to ensure that SSH traffic (typically on port 22) is allowed. Also, ensure that the Raspberry Pi has a valid IP address and is properly connected to the network. A faulty network cable or a misconfigured router can easily disrupt SSH connectivity.
The RemoteIoT platform goes a step further in enhancing security by providing features such as automatic key rotation and cleanup. It even cleans up the key immediately, so that a new public key setup is required for the next login attempt by the same user. This "one-time-use" key approach significantly reduces the risk of compromised keys being used for unauthorized access. Imagine a scenario where a developer's laptop is stolen, potentially exposing their SSH private key. With the RemoteIoT platform's automatic key cleanup, the stolen key becomes useless after a single login, preventing the thief from accessing your Raspberry Pi devices.
The RemoteIoT platform allows you to securely access and control your Raspberry Pi devices from anywhere in the world, enabling you to build innovative IoT applications and explore the possibilities of this exciting technology. Whether you're developing a smart home automation system, a remote monitoring solution, or a sophisticated industrial control network, the RemoteIoT platform provides the tools and security features you need to succeed. The platform abstracts away the complexities of SSH key management, allowing you to focus on building your applications rather than wrestling with security configurations.
While SSH is inherently secure, basic precautions should still be observed. Setting up SSH keys instead of passwords is an even stronger move. Always use strong passphrases to protect your private keys. Regularly rotate your SSH keys to minimize the impact of potential compromises. Implement multi-factor authentication for an extra layer of security. And keep your SSH client and server software up to date with the latest security patches. By adopting these best practices, you can significantly reduce the risk of SSH-related security incidents.
The RemoteIoT platform supports centralized management of SSH keys, simplifying the process of adding, removing, and rotating keys across your entire fleet of Raspberry Pi devices. Imagine having hundreds or even thousands of Raspberry Pi devices deployed in the field. Manually managing SSH keys for each device would be a Herculean task. The RemoteIoT platform automates this process, allowing you to manage SSH keys from a central dashboard. You can easily revoke access for departing employees, add new developers to the team, and enforce consistent security policies across your entire IoT deployment.
Setting up a RemoteIoT platform with SSH keys for Raspberry Pi involves several steps. First, install the necessary software on your Raspberry Pi, including the RemoteIoT agent and the SSH server. Then, configure your IoT platform to accept SSH connections, ensuring that the firewall is properly configured and that SSH key authentication is enabled. Finally, generate SSH key pair from RemoteIoT platform and add your public key on your raspberry pi using `ssh-copy-id` command, then test the connection using your platform. Following these steps will establish a secure and reliable remote access channel to your Raspberry Pi devices.
- Sdindische Filme Auf Hindi Action Drama Sonyliv Jetzt Ansehen
- Filmyfly Co Filmalternativen 2025 Was Sie Wissen Mssen

Unlock The Power Of Free RemoteIoT Platform SSH Key Raspberry Pi For IoT Projects

Mastering RemoteIoT Platform SSH Key Raspberry Pi Setup A Comprehensive Guide
RemoteIoT Platform SSH Key Free Access For Raspberry Pi The Ultimate Guide